
使用k3s快速搭建集群并部署一个nginx测试服务
# 环境
github加速:https://gitmirror.com/files.html
服务器:本次使用2台阿里云2H4G的Ubuntu@22服务器
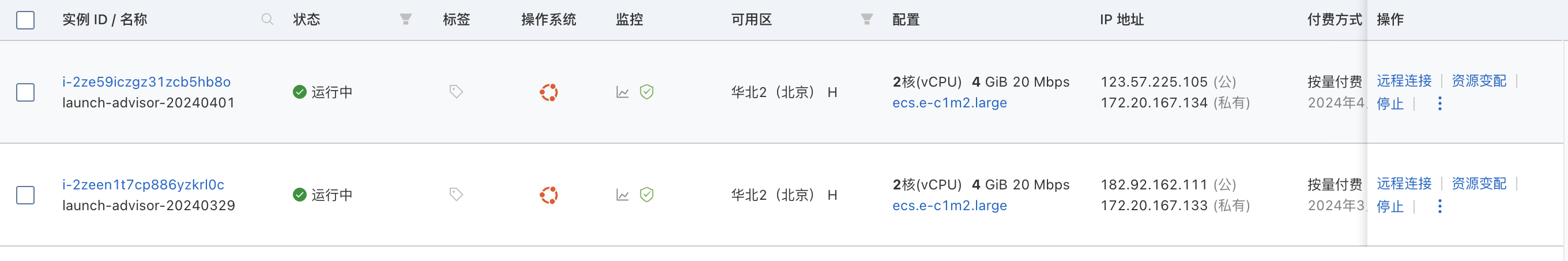
域名:1个备案测试域名 coooe.com,解析到任意一个服务器IP
或无需域名,使用hosts代理测试
# 安装
k3s官网安装文档:https://docs.k3s.io/zh/quick-start
# 在A主机安装Server(Master)节点
安装命令
➜ curl -sfL https://rancher-mirror.rancher.cn/k3s/k3s-install.sh | INSTALL_K3S_MIRROR=cn sh -
如果你只想在一台服务器上测试k3s,那么可直接跳到helm安装
安装完成后查看token用于Agent的安装
➜ cat /var/lib/rancher/k3s/server/token
K109ee008bb1cb5d0991d808d40d1e4aa96486d2572ad2b6442395d40c8737e80e1::server:881c91f124dc59156788da9b834ce9eb
取server:后面的token即可881c91f124dc59156788da9b834ce9eb
# 在B主机安装Agent(Node)节点
安装命令
curl -sfL https://rancher-mirror.rancher.cn/k3s/k3s-install.sh | INSTALL_K3S_MIRROR=cn K3S_URL=https://myserver:6443 K3S_TOKEN=mynodetoken sh -
修改命令中的myserver与mynodetoken的值后在B主机执行安装
➜ curl -sfL https://rancher-mirror.rancher.cn/k3s/k3s-install.sh | INSTALL_K3S_MIRROR=cn K3S_URL=https://123.57.225.105:6443 K3S_TOKEN=881c91f124dc59156788da9b834ce9eb sh -
安装完成后再A主机查看Node情况:
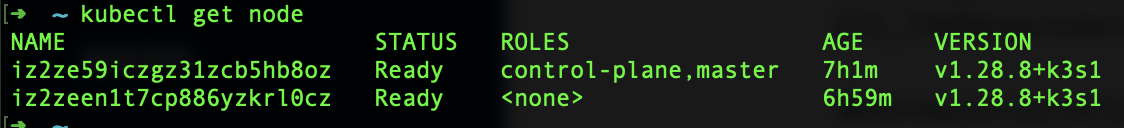
出现两个Node Ready就说明安装好了
# helm安装
helm官网地址:https://helm.sh/docs/intro/install/
在上面的文档中找到你的服务器对应系统的安装流程,下面是Ubuntu的安装流程
curl https://baltocdn.com/helm/signing.asc | gpg --dearmor | sudo tee /usr/share/keyrings/helm.gpg > /dev/null
sudo apt-get install apt-transport-https --yes
echo "deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/helm.gpg] https://baltocdn.com/helm/stable/debian/ all main" | sudo tee /etc/apt/sources.list.d/helm-stable-debian.list
sudo apt-get update
sudo apt-get install helm
然后复制k3s.yml到~/.kube/文件夹下即可
➜ cp /etc/rancher/k3s/k3s.yml ~/.kube/
测试helm命令:
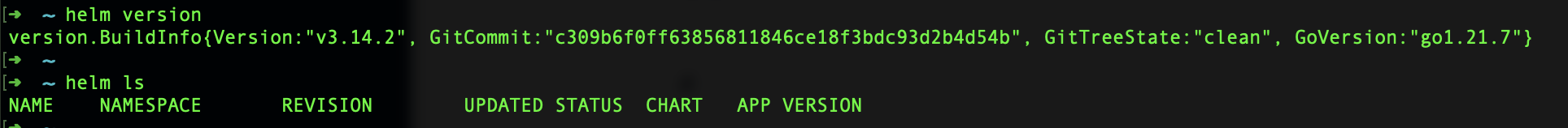
# 部署一个nginx服务
创建一个deployment.yml
这个yml包含Deployment、Service和traefik Ingress
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
selector:
matchLabels:
app: nginx
replicas: 2 # tells deployment to run 2 pods matching the template
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.14.2
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- port: 80
name: nginx
targetPort: 80
type: ClusterIP
selector:
# apply service to any pod with label app: nginx
app: nginx
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress-1
annotations:
spec.ingressClassName: traefik
spec:
rules:
- host: nginx.coooe.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80
部署yml
kubectl apply -f deployment.yml
如果没有域名,在本地的hosts添加代理
123.57.225.105 nginx.coooe.com
# 安装kube-explorer
github: https://github.com/cnrancher/kube-explorer
下载release后上传到服务器,执行启动kube-explorer
./kube-explorer --kubeconfig=xxxx --http-listen-port=9898 --https-listen-port=0
或
./kube-explorer --http-listen-port=9898 --https-listen-port=0
访问http://外网IP:9898
# 安装kuboard
docker run -d \
--restart=unless-stopped \
--name=kuboard \
-p 8081:80/tcp \
-p 10081:10081/tcp \
-e KUBOARD_ENDPOINT="http://内网或外网IP:80" \
-e KUBOARD_AGENT_SERVER_TCP_PORT="10081" \
-v /root/kuboard-data:/data \
eipwork/kuboard:v3
访问http://外网IP:8081
# 安装cert-manager,启用HTTPS访问你的服务
先创建一个cert-manager空间,以下都在cert-manager空间操作
cert-manager官网:https://cert-manager.io/docs/installation/kubectl/
1.安装cert-manager
# cert-manager.yaml
---
kubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/v1.14.4/cert-manager.yaml
2.安装alidns-webhook(cert-manager只支持几个国外的DNS服务商,其他服务商都是webhook来验证域名)
alidns-webhook: https://github.com/pragkent/alidns-webhook
# alidns-webhook-bundle.yaml
---
kubectl apply -f https://raw.githubusercontent.com/pragkent/alidns-webhook/master/deploy/bundle.yaml
3.存阿里云解析权限的AK/SK以备ClusterIssuer使用
# alidns-secret.yaml
---
apiVersion: v1
kind: Secret
metadata:
name: alidns-secret
namespace: cert-manager
resourceVersion: '5067'
type: Opaque
data:
access-key: xxx
region-id: xxx
secret-key: xxx
4.创建ClusterIssuer,域名验证
# clusterIssuer.yaml
---
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt-issuer # 自定义个名字
namespace: cert-manager
spec:
acme:
server: https://acme-v02.api.letsencrypt.org/directory # 这是acme线上环境地址
privateKeySecretRef:
name: letsencrypt-issuer # 自定义个名字
solvers:
- dns01:
webhook:
groupName: acme.yourcompany.com # 这个不要改,在 AliDNS-Webhook 里写死了
solverName: alidns # 这个固定写 alidns
config:
region: ""
accessKeySecretRef:
name: alidns-secret # 上面 alidns-secret.yaml 中的名字
key: access-key # 上面 alidns-secret.yaml 中的对应数据的 key,下同
secretKeySecretRef:
name: alidns-secret
key: secret-key
5.在需要的空间创建Certificate证书生成器,会自动生成证书并保存为Secret
比如切换到test空间
# Certificate.yaml
---
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: dev-coooe-tls # 证书名称
namespace: test # test空间
spec:
dnsNames:
- dev.coooe.com # 签证的域名(支持泛域名*.coooe.com)
issuerRef:
kind: ClusterIssuer
name: letsencrypt-live
secretName: dev-coooe-tls # Secret的名称
duration: 2160h
renewBefore: 360h
6.Ingress使用tls Secret使域名配置证书
# Ingress.yaml
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: whoami-https
namespace: test # test空间
annotations:
kubernetes.io/ingress.class: traefik
spec:
# 下面tls是关键配置
tls:
- hosts:
- dev.coooe.com
secretName: dev-coooe-tls # 使用证书的名称
rules:
- host: dev.coooe.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: whoami
port:
number: 80
7.设置http转https
Middleware.yaml
---
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: redirect
namespace: test
spec:
redirectScheme:
scheme: https
permanent: true
修改Ingress.yaml,添加annotations注解(值怎么写都没问题,不知原因)
annotations:
traefik.ingress.kubernetes.io/router.middlewares: test-redirect@kubernetescrd
查看是否生效
➜ curl -IL -X GET http://dev.coooe.com
HTTP/1.1 301 Moved Permanently
Location: https://dev.coooe.com/
Date: Fri, 19 Apr 2024 04:13:27 GMT
Content-Length: 17
Content-Type: text/plain; charset=utf-8
HTTP/2 200
accept-ranges: bytes
content-type: text/html
date: Fri, 19 Apr 2024 04:13:27 GMT
etag: "661e8b67-267"
last-modified: Tue, 16 Apr 2024 14:29:59 GMT
server: nginx/1.25.5
content-length: 615
8.访问 http://dev.coooe.com 或 https://dev.coooe.com
# 参考
k3s入门 - 知乎
k3s使用Let‘s Encrypt配置https入口部署 - 掘金
k3s 使用 Letsencrypt 和 Traefik 完成 https 入口部署 | Frytea
搜索话题 - Rancher 中文论坛
Rancher 高可用安装–Cert-Manager 签发 TLS 证书+4层 LB - 权威教程 - 搜索话题 - Rancher 中文论坛
k3s+rancher+gitlab+gitlab-runner+jenkins 持续集成系统在容器集群下的搭建 - 掘金
Kubernetes单机版部署 - 天朝读书人 - 博客园
Kubernetes(K3S)单机版部署 - 知乎
k3s+rancher 单机部署 - 小专栏
^_^成为第一个评论的人吧!







评论
昵称
邮箱 (回复通知)
站点
内容 (支持Markdown语法)